Published at block height 917041
Executive Summary
Within the next 10 to 20 years, experts estimate a cryptographically relevant quantum computer (CRQC) will be built, capable of seizing approximately 6.8 million bitcoin. These assets, valued at roughly CHF 600 billion and representing nearly a third of Bitcoin’s total supply, would become immediately vulnerable to theft. This quantum threat is not theoretical but a question of when, not if, presenting a systemic risk to the entire global digital infrastructure, for which Bitcoin is a critical, high-stakes case study.
A quantum attacker could derive the private keys to vulnerable addresses, granting them the ability to seize assets irreversibly. This vulnerability extends far beyond Bitcoin, affecting the entire digital economy, from international payment networks to the secure connections underpinning online commerce.
Technical solutions in the form of post-quantum cryptography (PQC) are maturing, with international standards bodies like the U.S. National Institute of Standards and Technology (NIST) standardizing new, quantum-resistant algorithms. The central challenge, therefore, is not technological innovation but sociopolitical coordination. Migrating a decentralized, global network like Bitcoin to a new cryptographic standard is a monumental undertaking fraught with risk.
The quantum threat forces a direct conflict between Bitcoin’s core principles: ownership guarantees versus censorship resistance. The community faces a dilemma: do nothing and risk a period of chaotic redistribution of wealth to attackers, or implement a protocol change that could be seen as confiscatory, potentially “freezing” un-migrated funds to prevent theft. This decision-making process, which must occur without any central authority, will be the ultimate test of Bitcoin’s governance model and its viability as a long-term store of value. The outcome will serve as a crucial lesson for governments and financial institutions as they prepare for the broader quantum transition.
1. Bitcoin: The Canary in the Coal Mine
While the quantum threat to Bitcoin is significant, it is merely the most visible element of a much larger, systemic risk to global security. The entire digital economy is built on public-key cryptographic systems that a CRQC will render obsolete. This vulnerability extends to the most critical digital infrastructure of society, threatening the foundations of government and traditional finance.
The global financial system, for instance, relies on cryptography for the integrity of international payment networks, the security of online banking, and the protection of sensitive customer data. A breach of these systems would trigger a catastrophic loss of trust and could result in staggering financial damage, with the Hudson Institute estimating potential indirect losses between $2 trillion and $3.3 trillion to the U.S. financial system alone [1]. Core internet protocols, electronic signatures, and secure government communications face the same existential threat.
In this context, Bitcoin serves as a crucial, real-time case study—a “canary in the coal mine” for the broader digital economy. Its transparent, high-stakes environment provides an early warning of the immense technical and sociopolitical challenges that all sectors will face during the mandatory transition to post-quantum cryptography. Understanding the specific nature of Bitcoin’s vulnerability is therefore essential for any leader preparing for this inevitable technological shift.
2. The Vulnerability: How Quantum Computers Break Digital Ownership
Bitcoin’s security relies on a “digital padlock” system. A public key acts as the lock, and only the corresponding private key can open it to authorize transactions. For today’s computers, deriving the private key from the public key is practically impossible. However, a CRQC will possess the ability to pick this lock, creating a critical threat to the network’s integrity by compromising the ownership of funds.
Seizing Assets with Shor’s Algorithm
The most direct threat comes from Shor’s algorithm, which enables a quantum attacker to reverse-engineer a private key from a public one, allowing for the outright theft of funds. The vulnerability manifests in two distinct scenarios, a long-range attack on past transactions and a short-range attack on current ones, as illustrated below.
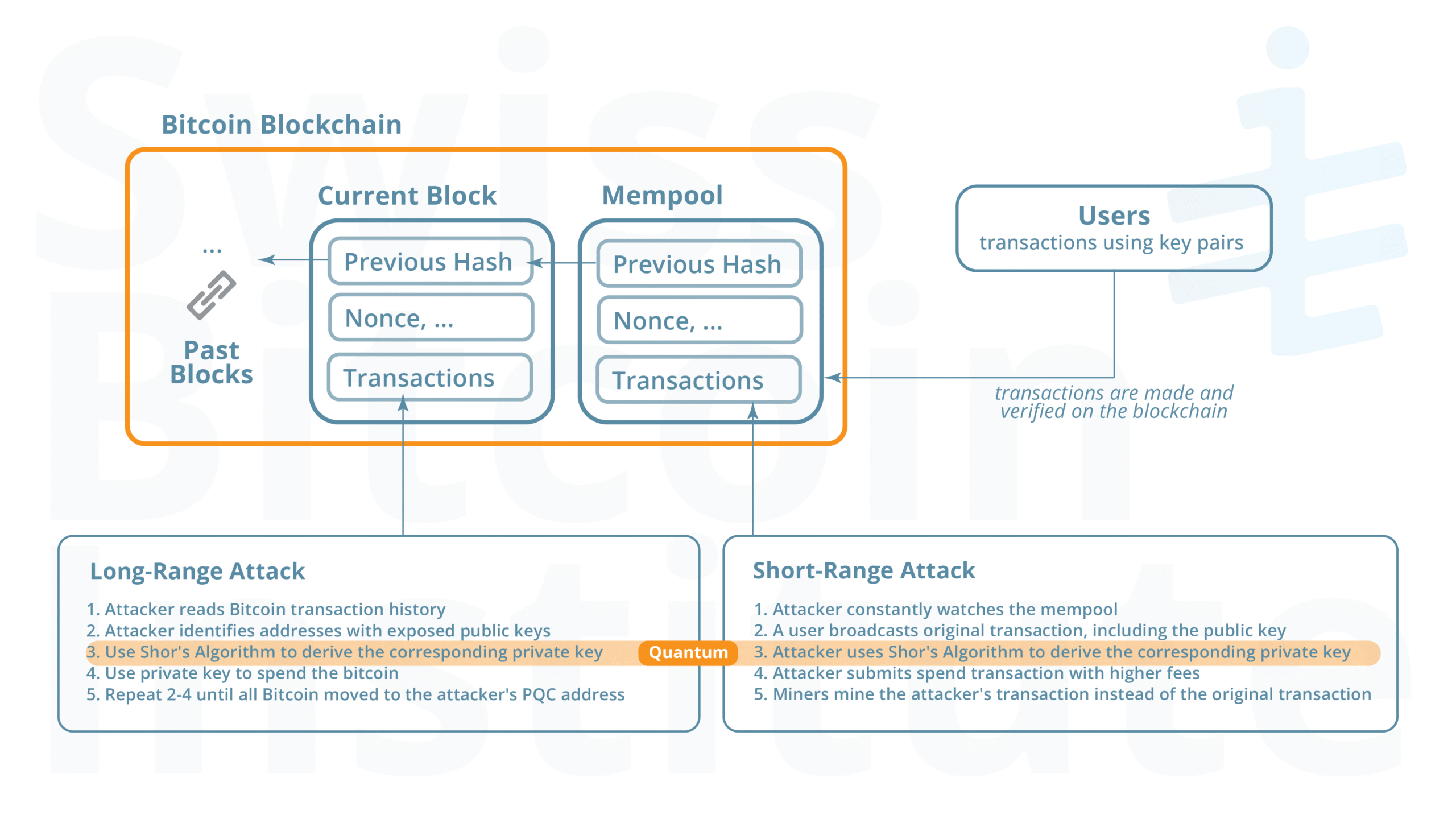
Figure 1: Long-Range vs. Short-Range Attack Vectors. The diagram illustrates the two primary methods a quantum attacker could use to steal bitcoin. Long-range attacks target funds where the public key is already exposed on the blockchain, while short-range attacks target new transactions as they are broadcast to the network.
The key difference is the time available to the attacker. For long-range attacks, the window is unlimited. For short-range attacks, the attacker has only a brief period—from minutes to hours—before a transaction is confirmed on the blockchain to calculate the private key and execute the theft.
The scale of this risk is substantial, according to research presented by Dr. Anthony Milton at the Quantum Bitcoin Summit 2025 [2], and detailed in Project 11’s Bitcoin At Risk list [3]. They estimate 6.8 million bitcoin (ca. CHF 600 billion as of today) vulnerable to long-range attacks, representing nearly a third of Bitcoin’s total supply. A successful, large-scale attack would trigger an irreversible transfer of wealth on an unprecedented scale, likely causing a market collapse and severely undermining confidence in the entire digital asset class. The table below provides a breakdown of this exposure across different types of Bitcoin accounts (address types), some of which are more vulnerable than others.
Table 1: Estimated bitcoin at risk from long-range quantum attacks
| Address Type | Usage | BTC at risk |
| Address Reuse (P2PKH, P2SH, P2WPKH, P2WSH) | Always | 4.75M |
| P2PK | 2009-2012 (incl. Satoshi’s coins) | 1.72M |
| P2TR (keypath) | From 2021 (Taproot activation) | 0.17M |
| BCH Fork Exposure | 2017 and later | ~0.15M |
| P2MS | 2012, and recent renewed usage by the Stacks protocol | ~69 |
It is important to note that this vulnerability figure is a snapshot in time. A significant portion of these at-risk funds will likely be moved to safer addresses by their owners long before a CRQC materializes. However, a substantial number of coins are considered permanently lost, creating an irreducible floor of risk. As of 2025, estimates suggest this pool of lost assets ranges from 2.3 to 4 million BTC, according to BitGo [4], a figure that includes the roughly 1.1 million bitcoin attributed to Satoshi Nakamoto. While it is currently unknown what portion of these lost coins are in quantum-vulnerable address types versus safer formats, the remainder represents a historic prize for a quantum attacker: the ability to reclaim billions of dollars in dormant assets, effectively bringing them back into circulation under new ownership.
The CRQC Threshold: Qubits, Timelines and Technical Hurdles
Executing Shor’s algorithm at a scale relevant to attacking Bitcoin requires surmounting significant technical hurdles, which informs the 10-to-20-year timeline for a CRQC. The primary challenge is the gap between today’s noisy, error-prone physical qubits and the stable, error-corrected logical qubits required for complex calculations. Creating a single logical qubit can demand hundreds to thousands of physical qubits, and current quantum computers possess only a few hundred physical qubits.
The journey to a CRQC is a multi-stage progression, with industry leaders pursuing different strategies to overcome the complex engineering hurdles. For example, projects like Google’s “Willow” and Microsoft’s “Majorana” highlight competing approaches to achieve the necessary scale and stability for a fault-tolerant machine.
This hardware race is critical due to a counter-intuitive fact: breaking today’s cryptography is not the hardest problem for a quantum computer, but one of the easiest. Preliminary results from DARPA’s Quantum Benchmarking Initiative illustrate this starkly, placing the threat to digital security in the near- to mid-term feasibility window for a CRQC.
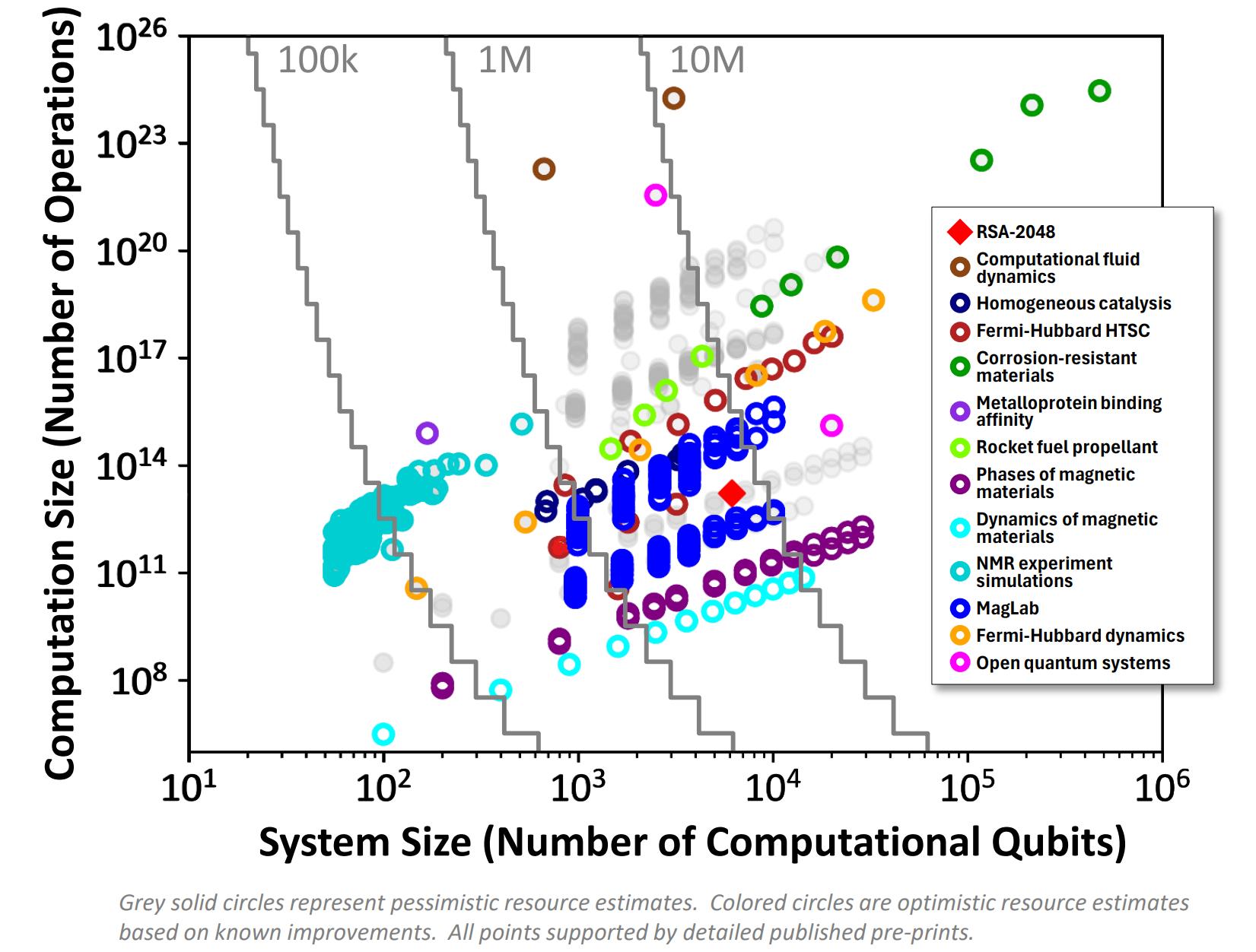
Figure 2: DARPA’s Quantum Benchmarking Results. The chart plots various quantum applications by required system size (qubits) and computation size (operations). Note that security decryption tasks like breaking RSA and ECDSA (solid red diamond and circle, respectively) are located in the lower-left quadrant, indicating they are among the least difficult problems for a CRQC. Source: DARPA QBI Proposers Day, 2024. [5]
This makes the threat to Bitcoin particularly acute. Still, while estimates vary as research progresses, Chaincode Labs research suggested a CRQC would need approximately 1,000 logical qubits to succeed [6]. In terms of physical hardware, this could translate to hundreds of thousands or millions of physical qubits—a scale far beyond current capabilities. The process of converting vast numbers of physical qubits into a few thousand stable, usable logical qubits is the key bottleneck, making the development path a series of complex engineering achievements.
This hardware gap and the multi-step development process are the basis for the consensus timeline. It is a race between the rapid development of quantum hardware and algorithmic improvements that reduce the number of qubits required. While an immediate threat is unlikely, the trajectory of progress is clear, making the development of a CRQC a question of when, not if.
A Note on Mining: The Low-Risk Threat of Grover’s Algorithm
While quantum computing’s effect on mining is often discussed, leading research indicates the threat is largely theoretical and economically impractical. Although Grover’s algorithm could theoretically speed up mining, the advantage is not significant enough to threaten the network’s security. Furthermore, a general-purpose quantum computer would be economically impractical for mining, unable to compete with the cost and energy efficiency of the global network of hyper-specialized ASIC hardware.
3. Bitcoin’s Response: Technical and Sociopolitical Challenges
3.1 The Solutions Landscape
The solution to the quantum threat is clear: migrate Bitcoin to a post-quantum cryptography (PQC) standard. But the first-generation algorithms present major strategic trade-offs, making them a poor fit for a resource-constrained system like Bitcoin.
First, their massive size is a primary hurdle. Integrating leading candidates—like the NIST-standardized CRYSTALS-Dilithium and SPHINCS+—would drastically increase blockchain storage needs and transaction fees, as their digital signatures are 35 to 120 times larger than those used today. Second, these new algorithms are immature. They lack the decades of real-world, adversarial testing that hardened current standards, creating a significant risk of unforeseen implementation bugs. This forces a difficult trade-off: adopt today’s quantum-safe standards or wait for more efficient, battle-tested solutions to emerge.
This “readiness versus perfection” dilemma has led to the emergence of three distinct categories of solutions being debated within the community, each with its own strategic advantages and disadvantages.
1. Comprehensive Protocol Upgrades: This category represents the ideal long-term solution: a full-scale upgrade of Bitcoin’s code to introduce a new, quantum-resistant address type. Proposals like the “Pay to Quantum Resistant Hash” (P2QRH) concept aim to create a permanent, native fix. However, this approach requires achieving near-unanimous global consensus, a process that is notoriously slow and difficult in a decentralized ecosystem, making it a viable but distant goal.
2. Stop-Gap Measures: Recognizing the difficulty of a full upgrade, several proposals have been developed as targeted, short-term interventions to buy time. Proposals like “Liferaft” and “Hourglass” aim to mitigate the most immediate risks by either temporarily shielding transaction data or deliberately slowing down the spending of vulnerable funds to thwart a rapid, large-scale theft. Their advantage lies in being less contentious and faster to implement, but they do not solve the underlying vulnerability.
3. Off-Chain Solutions: A third category of solutions bypasses the need for network-wide consensus entirely. Projects like the “Yellowpages” registry propose an offchain opt-in system where users can cryptographically link their legacy addresses to new, quantum-safe ones, providing a way to migrate Bitcoin to a post-quantum scheme without immediate network upgrades. This approach is fast and flexible but introduces new trust assumptions. It relies on a centralized or federated entity, a model that runs counter to Bitcoin’s core ethos of decentralization and would create new high-value targets for attackers.
These divergent approaches highlight the central challenge: there is no single, easy path forward. The choice is not just about which technology to adopt, but about which trade-offs the community is willing to accept between security, performance, and its own foundational principles.
3.2 A Test of Governance: Bitcoin’s Proactive Crisis Moment
The quantum threat presents a profound philosophical test for Bitcoin, forcing the community to confront a conflict between its core principles. More importantly for institutional observers, it serves as a critical case study in decentralized crisis management. Bitcoin’s genesis block famously references a bailout, rooting its existence in the chaotic aftermath of the 2008 financial crisis. That crisis was managed through a series of reactive, top-down interventions that created a legacy of moral hazard and eroded public trust. The quantum challenge is Bitcoin’s own systemic crisis, but with the crucial advantage of being foreseeable. It presents the ecosystem with an opportunity to demonstrate a more transparent, proactive model of crisis management.
The core of this governance test is a dilemma with striking parallels to the choices faced by policymakers in 2008:
- A Chaotic Redistribution of Wealth, violating Bitcoin’s ownership guarantees. If no action is taken, the default outcome is a significant, non-market transfer of wealth to the first quantum attackers. Just as the 2008 bailouts represented a chaotic redistribution of wealth from the public to a select few via political decree, the “do nothing” approach in Bitcoin would result in a chaotic redistribution from many holders to very few via a technical attack. The anticipated impact on the price of bitcoin would be relevant to all stakeholders, not solely the affected parties.
- Violating Bitcoin’s censorship resistance. An alternative option is to implement a protocol change that would “freeze” or “burn” un-migrated funds, thereby preventing theft. This option is analogous to the most extreme measures considered or enacted during financial crises: the imposition of capital controls. Just as limiting bank withdrawals violates the fundamental principle of property rights and free access to one’s own capital, a protocol-level freeze would violate Bitcoin’s core principle of censorship resistance in the name of economic security, setting a dangerous precedent.
For institutional investors, the stakes of this decision are immense. Their confidence hinges on the network’s ability to navigate a systemic crisis in an orderly, predictable manner, avoiding the very kind of damaging, ad-hoc consequences that defined the response to the 2008 crisis. A successful, consensus-driven migration would be a powerful demonstration of the system’s maturity. Conversely, a failure to act, or a schism that fractures the network, would signal that its governance model is incapable of handling a foreseeable threat, severely undermining its attractiveness as an institutional-grade asset.
In summary,
the quantum threat forces a direct conflict between Bitcoin’s core principles: ownership guarantees versus censorship resistance. The true challenge is twofold: it is both a test of technology and governance. The results of this test will define the future of digital assets.
4. The Race to Readiness: Global Policy and the Quantum Transition
4.1 The Strategic Imperative: “Harvest Now, Decrypt Later”
The global policy response to the quantum threat at large is driven by an alarming and immediate risk known as “harvest now, decrypt later.” Adversaries, including nation-state actors, are already intercepting and storing large volumes of encrypted data today. Their intention is to decrypt it once a CRQC becomes available, making the threat immediate for any data that must remain confidential long-term, from state secrets to corporate intellectual property.
A crucial element of the game theory at play is that a successful quantum attacker has a strong incentive not to reveal their capability by attacking a high-profile target like Bitcoin. Doing so would serve as a public “quantum canary,” forcing the entire world to accelerate its PQC migration. Instead, they would likely use the technology in secret against less detectable, high-value targets.
4.2 Policy in Practice: The Swiss and EU Context
Governments globally are not idle. A clear policy consensus is forming around a 2035 deadline for migrating critical national security and economic systems to post-quantum standards, a timeline adopted by both the United States and the European Union. For financial institutions in Switzerland and the EU, this abstract deadline is rapidly becoming a concrete regulatory challenge.
- The Swiss Digital Asset Blind Spot: Switzerland exemplifies this challenge. While a global leader in quantum research, with significant public investment through the Swiss Quantum Commission, an entity created to coordinate national research and position Switzerland as a global leader in the field, its official financial policy shows a critical gap. The recent action plan for quantum readiness from the Swiss Financial Innovation Desk (FIND), for example, does not include digital assets [7]. This creates a strategic risk for a nation that is a major global hub for both finance and the crypto industry, leaving its world-leading wealth management sector and its burgeoning ‘Crypto Nation’ ecosystem unprepared.
- The EU Regulatory Horizon: In the European Union, the path forward is becoming clearer. Post-quantum readiness will inevitably be integrated into existing and forthcoming regulatory frameworks. For financial service providers, compliance with the Digital Operational Resilience Act (DORA) should be expanded to include resilience against quantum threats. Similarly, future iterations of the Markets in Crypto-Assets (MiCA) regulation are expected to incorporate quantum-safe standards for digital asset issuers and service providers. The transition to PQC is therefore not merely a technical upgrade; it is a future compliance mandate.
For Swiss policymakers, the quantum threat should be framed alongside other established national strategic risks. Switzerland has robust, long-term national strategies for protecting critical infrastructure against threats like major cyberattacks (National Cyberstrategy, NCS) and energy shortages (Organisation for Power Supply in Extraordinary Situations, OSTRAL). The systemic risk posed by the quantum transition to the nation’s financial and digital infrastructure requires a similarly proactive and coordinated national strategy to avoid a future crisis.
This evolving landscape presents a strategic opportunity. The jurisdiction that first provides clear regulatory guidance on quantum-safe digital assets will establish a significant first-mover advantage, positioning itself as the premier hub for the next generation of secure digital finance. The following table provides a summary of the key milestones and their significance, illustrating that the path to a quantum-resistant future is already underway.
Table 2. Quantum milestones and significance
| Year | Milestone | Significance |
| 2016 | NIST PQC standardization competition starts | Initiated a global effort to find quantum-safe cryptographic standards. |
| 2024 | NIST releases “FIPS 204 & 205” | Established the first official standards for post-quantum digital signatures. |
| 2030-2035 | US deadline for PQC migration | Provides a clear roadmap and external pressure for the transition of vulnerable systems. |
| 2035+ | Estimated timeline for CRQC | Represents the period when a cryptographically relevant quantum computer could emerge. |
5. Strategic Recommendations for a Post-Quantum Future
The quantum threat requires a proactive and tailored response from all major stakeholders. Navigating the transition to a post-quantum world will depend on leaders in business, finance, and government understanding their unique risks and strategic priorities.
For investors and asset owners, from individuals to corporate treasuries, the primary risk is the direct loss of funds, a threat compounded by potential governance gridlock that could delay a network upgrade. Their strategic priority must therefore be twofold: proactively securing their current holdings while simultaneously helping to drive community consensus on a migration path. This begins with immediate, practical steps like migrating holdings away from legacy, quantum-vulnerable address types and enforcing strict no-address-reuse policies. Beyond individual security, these stakeholders can use their influence to fund targeted research into viable PQC solutions and engage directly in governance debates to help forge the necessary consensus for a network-wide solution.
Financial institutions, including custodians, exchanges, and banks, face the risk of fiduciary failure and catastrophic security breaches if they cannot safeguard client funds. Their core priority is to achieve operational readiness for a network-wide cryptographic transition. This requires building the technical infrastructure to handle a mass migration event, such as generating new quantum-resistant addresses for all clients at scale. Furthermore, they must mandate that all custodial and wallet partners demonstrate a concrete plan for supporting a potential quantum-resistance fork. Crucially, this internal preparation must be matched with a clear external communication strategy to educate clients on the threat and the institution’s plan to protect their assets.
For governments and regulators, the principal risk is the destabilization of the financial system, driven by a quantum shock to the digital asset market and its potential contagion effects. The strategic priority should be to develop informed and targeted oversight that addresses the unique challenges of a decentralized, open-source protocol. A pragmatic first step is not to direct, but to empower. By allocating public funds to support the independent, open-source research and development of quantum-resistant solutions for Bitcoin, they can accelerate a solution without compromising the ecosystem’s decentralized ethos. This can be complemented by modeling the potential impact of a quantum attack on Bitcoin as part of national financial system stress tests to prepare for the worst-case scenario.
References
- Alexander W. Butler and Arthur Herman. “Prosperity at Risk: The Quantum Computer Threat to the US Financial System”, Hudson Institute, April 2023. Link
- Presidio Quantum Bitcoin Summit, YouTube Playlist, July 2025. Link
- Project Eleven Vulnerable Bitcoin Tracker. Project Eleven. Updated 28. September 2025. Link
- Bitcoin’s Invisible Burn: Lost Coins Outpace New Supply. BitGo, August 2025. Link
- Quantum Benchmarking Initiative (QBI), Preliminary results from Quantum Benchmarking. December 2024. Link
- Dr. Anthony Milton and Dr. Clara Shikhelman. “Bitcoin and Quantum Computing: Current Status and Future Directions”, Chaincode Labs, May 2025. Link
- Swiss Financial Innovation Desk (FIND). “Action Plan to a Quantum-Safe Financial Future”, March 2025. Link
The Swiss Bitcoin Institute promotes sound, independent research on Bitcoin. Opinions expressed by Fellows are theirs and do not necessarily reflect those of the Swiss Bitcoin Institute.